User name and
password doesn’t cut it anymore in the world of online financial
transactions. New federal rules call for multi-factor authentication
schemes to combat growing threats. The latest multi-factor measures
focus on biometrics, advanced analytics, and out-of-band techniques
utilizing smartphones.
Man-in-the-Browser attacks
One serious threat on the horizon is the man-in-the-browser (MITB) attack. In this example,
1. Alice requests transfer of $1,000 to Bob.
2. MITB alters transfer request to transfer $21,000 to Fred.
3. MITB submits fraudulent request to bank.
4. Bank requests confirmation of transfer of $21,000 to Fred.
5. MITB alters confirmation page to present user with original request.
6. Alice reviews the transaction details and confirms request.
7. Bank transfers $21,000 to Fred.
Man-in-the-middle attacks use various social engineering techniques to intercept user credentials and commit fraudulent actions completely under the radar. How MITM attacks work:
1. User clicks on link in a phishing email, goes to MITM site and enters credentials (including token-generated one-time password).
2. MITM site connects with bank site and impersonates legitimate user using phished credentials.
3. Bank site grants MITM account access.
4. MITM displays phony page stating system is unavailable, or waits until user wants to log off, then displays phony page confirming log-off.
CA Arcot’s RiskFort is built to prevent these types of attacks
CA Arcot’s RiskFort provides a sophisticated risk evaluation process that assesses the risk of a specific transaction and increased the level of authentication required.
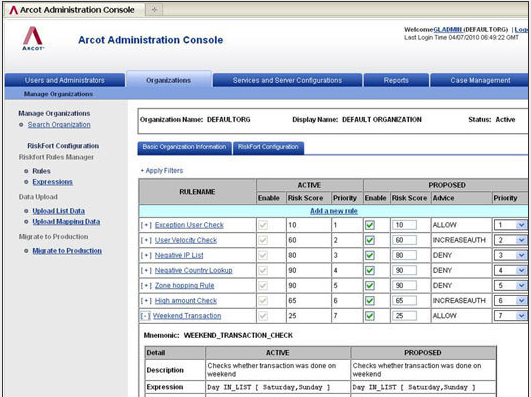
Arcot Administrative Console
CA Arcot RiskFort administrator console is where the rules and risk-scores are created, edited, and managed.
WebFort authentication server
The CA Arcot WebFort authentication server applies authentication policies, issues notifications and alerts and creates reports.
From the user perspective
With the CA ArcotID secure software credentials, users gain improved security of multi-factor authentication without changing their familiar user name and password log-in experience. Unlike other multi-factor authentication methods that often require extra steps such as obtaining and typing in a one-time-password, CA ArcotID strengthens the user name and password authentication process by transparently providing software-only, public key infrastructure-based, multi-factor authentication.
Confident Technologies uses the power of the grid
The first time users enroll with a website or online business, they select a few authentication categories that they can remember such as dogs, cars, flowers, etc.
Out-of-band authentication
When two-factor authentication is needed, a randomly-generated grid of images displays on the user’s mobile phone (using MMS, WAP, or an SMS hyperlink that is opened within the mobile browser).
Tomatoes.
The specific images displayed are different every time, but the users’ categories are always the same; for example, the category FOOD shows tomatoes on the first grid and strawberries on the second grid. This makes it difficult for others to determine users’ secret categories.
Tap or type to verify
Users authenticate by correctly identifying which images fit their chosen categories. They can tap the appropriate images on the touch screen display or, if users don’t have a touch screen device, they can type the corresponding letters using their mobile keypad (optionally, letters can be displayed).
Successful authentication
Screen displays successful authentication text and icon (check mark in green circle). Even if others gain possession of the mobile phone or intercept the communication, they cannot authenticate because the one-time password is encrypted within the images.
Entrust offers multiple factors
One method of multi-factor authentication is Transaction Verification, where Entrust does real-time transaction verification on users’ mobile devices.
Soft tokens
Mobile soft tokens placed on mobile devices can serve as an authenticator to enterprise networks, applications, and resources.
Device certifications
Entrust also delivers digital certificates deployed directly to mobile devices so organizations can authenticate the device before it connects to a network.
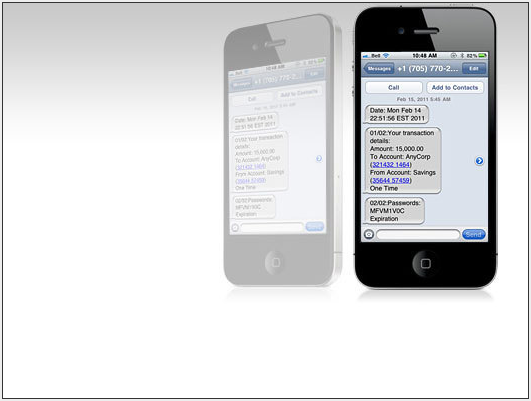
SMS One-time passcodes
eGrid authentication
Entrust’s patented grid-based authentication is yet another wrinkle of multi-factor authentication.
PhoneFactor’s out-of-band answer
Once users enter their username and password, PhoneFactor instantly places an automated phone call to the users’ registered phone number. Users simply answer the call and press # (the pound sign) to complete their login.
Adding a PIN to the pound
PhoneFactor can also provide an additional layer of protection by requiring users to enter a PIN to authenticate.
Security-based texting
PhoneFactor also allows users to authenticate via SMS text; that is, PhoneFactor sends users a one-time passcode in an SMS text message, then users simply reply to the text message with the pass code to authenticate.
Three-factor voice-based authentication
Biometric voice authentication delivers the strongest level of authentication. PhoneFactor simultaneously verifies something users have (their telephone) and something users are (their voiceprint) for the second and third factors of authentication.
Fraud Alert
Users can instantly report fraudulent activity on their accounts by choosing the fraud alert option during the authentication call, which blocks access to their account and triggers an email to your security team.
Source: NetworkWorld.com





















0 comments:
Post a Comment